

search engine that allows customers to search for unlawful merchandise from many Darknet Markets without delay. As a end result, illicit info might be much easier to seek out for any cybercriminal. Some of the popular darknet browsers are Freenet, Tor, GNUnet, I2P, OneSwarm, RetroShare, and so on. A different community that’s encrypted and is created upon the existing web is Darknet. It can only be accessed by utilizing some specific configuration of the tools and software.
IAPP Canada Privacy Symposium Find solutions to your privacy questions from keynote speakers and panellists who’re experts in Canadian knowledge protection. IAPP Asia Privacy Forum World-class discussion and education on the highest privacy points in Asia Pacific and across the globe. (P.S.R.) P.S.R. presents the most effective of the most effective in privateness and safety, with revolutionary cross-schooling and stellar networking. Sponsor an Event Increase visibility in your group—check out sponsorship opportunities today.
Rather, the websites that commerce in such “merchandise” are segregated from mainstream cryptomarkets, in much the same method convicted paedophiles are segregated from mainstream jail populations. Login details of streaming sites such as Netflix bought on the darknet markets for low costs had been also reported. The second level, the profound cloud, is a network the place data is stored in an inaccessible database . The data are usually sensitive and personal and are therefore not accessible.
Speak at an IAPP Event View our open calls and submission directions. Accepted for publication on the 19th of July 2018 In latest years, the Darknet has become one of the most discussed matters in cyber safety circles. Current educational research and media reports have a tendency to highlight how the nameless nature of the Darknet is used to facilitate legal actions. This paper stories on a latest research in four Darknet boards that reveals a special facet of the Darknet. Drawing on our qualitative findings, we suggest that many customers of the Darknet may not understand it as intrinsically criminogenic, regardless of their acknowledgement of various sorts of legal activity on this community.
Originally developed by the U.S. government, it’s now seen as a dangerous system that often is used for illegal or unethical functions. There are different encrypted networks similar to TOR and so they all together type Darknet. The data which официальный адрес магазин гидры на тор are purposefully unrevealed and is not attainable by way of any normal web browsers is termed as darkish web. Dark Web is generally used for unlawful and nefarious activities. The content inside Dark Web is normally discovered using the Tor community.
The connection could be encrypted between the Tor browser and the Tor exit, therefore what the company VPN sees is simply encrypted tor visitors. I solely need browser level protection, which is why I use TOR, in any other case I want all traffic to go through my network normally. Adding every utility to ProtonVPN’s bypass filter is tedious to say the least.
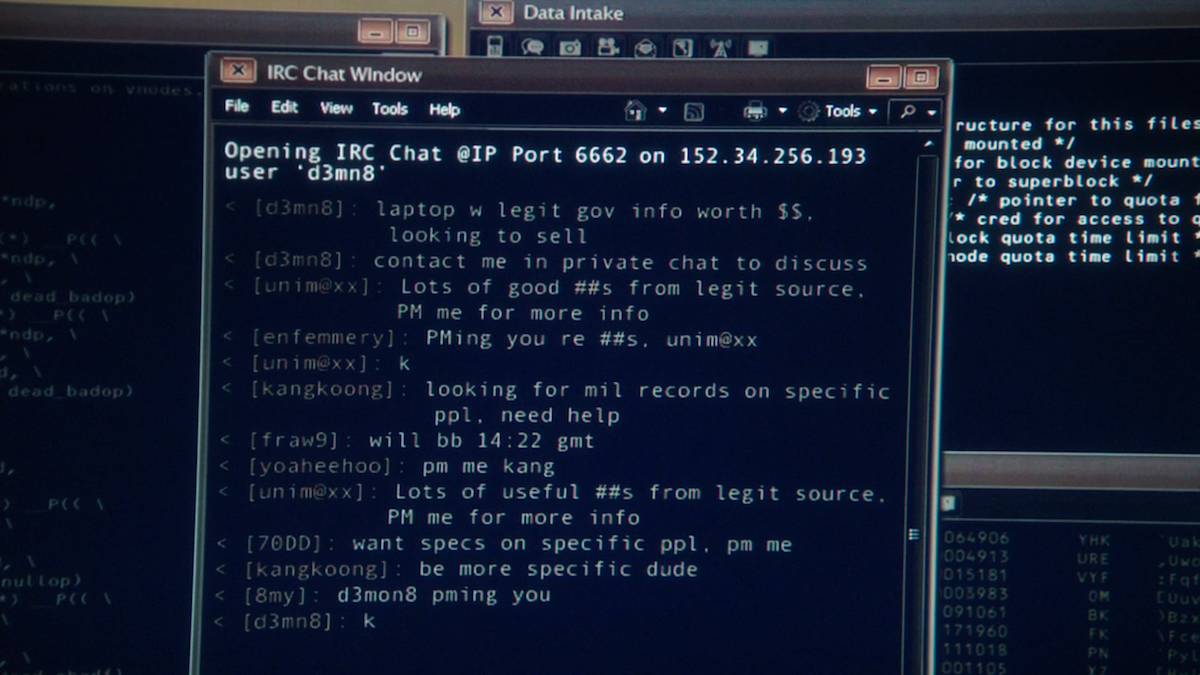
And any employee with entry to the Tor browser can solicit anonymous bids for sensitive company data, code, or access. The bar to accessing felony expertise and digital capabilities has by no means been decrease. As the darknet becomes mainstream, more people might decide to actively cut up their online actions between a public face on the open web and a personal face on the darknet. Our lives have become permeated with customized companies and technology, permitting strangers to see intimate details of our lives through social media and search engines like google.